Table of contents
In today’s world, everyone has created a profile of themselves online at one point or another with the help of third parties. Before the blockchain era, these third parties kept each person’s profile in their databases. Information in these databases often gets sold to marketing companies. Worse, these third parties have had data breaches over the years. The data breaches have caused the information of multiple users to be available to hackers with malicious intent.
In this guide, I will explain how you can use the blockchain to secure your profiles online and prevent them from being sold to marketing companies.
What Is a Digital Identity?
A digital identity is any identity on the internet assigned to an individual or organization. You can use a digital identity to identify a person or organization and authorize them to access certain resources in the digital world.
A digital identity can include a range of attributes such as a name, password, email address, address, phone number, and others. Individuals and organizations can use their digital identities for several purposes, such as performing financial transactions, creating a profile on a music app, and logging in to a social media app.
There are multiple ways a person or an organization can verify their identities, such as:
Biometrics
Username
Password
Two-factor Authentication
Disadvantages of Centralized Forms of Digital Identity
Digital Identity makes identification easier and portable, but traditional (centralized) forms of digital identity, as popularly used today, have a lot of loopholes that can lead to privacy and security issues. Some of these loopholes include:
1. Centralized Control
In a traditional or centralized form of digital identity, a single authority often controls the data provided by the users. As a result, users have very little control over their digital identity.
The single authority that controls users' digital identity often makes them abide by their policies before they can access resources. Centralized control can also cause problems with transparency and accountability because users can seldom trust the authority in charge of their digital identity.
2. Single Point of Failure (SPOF)
Single Point of Failure (SPOF) means that one part of a system's failure or malfunction can make every other part fail. In a centralized form of digital identity, the system is very prone to cyber-attacks.
It is also important to note that centralized digital identity solutions which do not use a user's biometrics are very easy to clone with the help of technologies like deepfake.
3. Limited portability
In this context, limited portability refers to the inability of a user to transfer their digital identity from one system or service to another. A user might have access to some digital resources under a particular company but cannot access digital resources with another company. This scenario will force users to create multiple digital identities across different platforms. Having multiple digital identities is highly insecure because it makes the users' information available in different systems prone to cyber-attacks.
Digital Identity and the Blockchain
The blockchain provides a secure way of creating digital identities. It solves the problems associated with centralized forms of digital identities by giving users total control over their digital identities. Users can store their information without fear of a data breach or having their data sold to marketing companies. The blockchain utilizes decentralized identifiers to ensure data security and provide a flexible digital identity solution.****
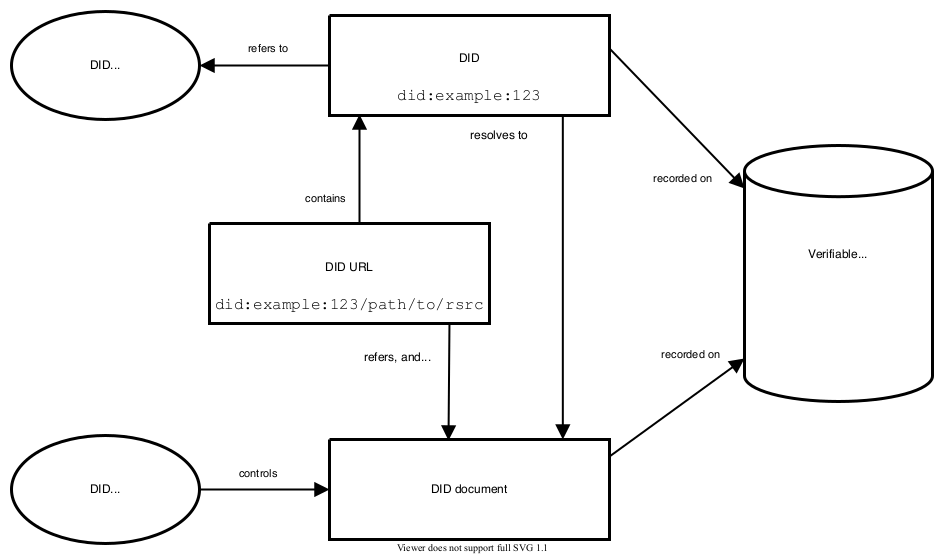
What are Decentralized Identifiers?
Decentralized identifiers (DIDs) are identifiers stored on a decentralized distributed ledger technology. These identifiers often refer to an entity, like an individual, organization, abstract entity, etc, defined by the controller. The entity has complete control over the usage of the identifier and the ability to stop it from being used.
Decentralized identifiers are easy to check, trustworthy, and easy to access. With decentralized identifiers, With decentralized identifiers, users have flexibility and independence over their digital identity. This article gives a detailed explanation of decentralized identifiers.
Features of Decentralized Identifiers
Decentralized identifiers have several notable features that are distinguishable from centralized forms of digital identity. Some of them are:
1. Control
Unlike centralized forms of digital identities, users have complete control of their digital identities in the blockchain with the help of DIDs.
2. Security
The blockchain is designed to be safe, secure, and impenetrable. These features make it impossible for hackers to steal users' personal information. Social engineering attacks can, however, be used to gain unauthorized access to a person’s information.
3. Privacy
The user has total control over his identity data and to whom he chooses to give them.
4. Ease of Use
Users can create and manage their digital identity across different decentralized apps and platforms. Users will enjoy a seamless experience across different blockchain platforms with this ability.
5. Persistent
There is no single point of failure since the data is stored on all the nodes on the blockchain.
How do Digital Identity Solutions Work?
Decentralized distributed ledger technology is used to manage an entity's identity using smart contracts called decentralized identifiers (DIDs). The user's identity data is stored in an immutable and securely encrypted blockchain. The user accesses their identity using a private key, while verifiers use a public key provided by the user. The identity smart contract can contain bio-data, biometrics, and other information.
By using Oracles, real-world data such as documents and certificates can be collected and stored on the blockchain using upgradeable smart contracts, ensuring that a user's data is up-to-date.
The World Wide Web Consortium (W3C) has proposed recommendations for building digital identity solutions, including technical proposals for creating such solutions.
Digital Identity Solutions Across Smart Contract Platforms
Solana → Civic, ONTO Wallet, IdentitySwap, Galaxy
Cardano → Atala PRISM, IdentityToken, Blockademia, dHealth, IAMX.
Ripple → Global ID
Avalanche → Galaxy
Polkadot → Dock, KILT Protocol, Litentry, Zero.IO, Peaq, NFT Mart.
Cosmos → Identity Service, Cosmos DID,
Algorand → Securecets, MailChain, Verida, DIZME Ecosystem
Fantom → Galaxy
Telos → Dmail, DecideVoter,
Internet Computer → ICNaming, Internet Identity.
Conclusion
In conclusion, blockchain technology provides a secure way of creating and managing digital identities. It eliminates the problems associated with centralized digital identities, such as lack of control, security issues, and limited portability.
With decentralized identifiers, users have complete control over their digital identities, making it impossible for marketing companies to access their information or for hackers to steal it.
Furthermore, digital identity solutions built on smart contract platforms such as Ethereum, BNB Chain, and Polkadot are already available, making it easier for users to create and manage their digital identities across different blockchain platforms.